This section describes how to obtain and install a signed server certificate from Active Directory for 802.1X authentication. This section contains the following information:
Provides a detailed information about any issue encountered when connecting the clients to Aruba Central network. Troubleshoot client connectivity issues diagnosed through AI Search Bar, offline clients in the network, datapath of WLAN clients, client health issues, and client roaming issues. Aruba Airwave Doesn't Generate Private Key Cod4 Cd Key Generator Razor1911 Download. 12/9/2020 Generate random alpha, numeric, or both, CD keys for software.
About Certificates in Policy Manager Deployments
A certificate is a file that makes it possible for network devices to communicate with each other securely. For example, in Policy Manager deployments, certificates are provided for all devices involved in authentication, such as client laptops, smart phones, Mobility controllers, Mobility Access Switches, AOS switches, Policy Manager servers, and so on.
Certificates help you communicate securely in two ways:
Certificates help devices verify the identity of other devices.
Certificates enable devices to use encryption to securely communicate with each other.
When a certificate is created, two keys are generated; the private key and the public key. The private key is always stored securely and never sent out. If the private key is compromised, the entire security framework established by the certificate is compromised. The public key contains important information about the certificate owner. The public key is inside the file that is sent to all devices that wish to communicate with the certificate owner. This file contains additional information about the identity of the certificate owner’s device.
Public and private key pairs are generated so that any data encrypted by one of these keys can only be decrypted by the other corresponding key. Any data encrypted by the private key can only be decrypted by the corresponding public key. Conversely, any data encrypted by the public key can only be decrypted by the corresponding private key.
Aruba Airwave Doesn't Generate Private Key Godaddy
When Certificate Usage Is Necessary
There are three common Policy Manager deployments in which certificates are necessary :
When using HTTPS to manage network devices such as mobility controllers, mobility access switches, AOS switches or Policy Manager servers.
During captive portal authentication.
When using 802.1X authentication.
How 802.1X Authentication Uses Server Certificates
When an employee attempts to log into his laptop, the EAP-PEAP authentication process begins:
1. The Policy Manager server sends the server certificate to the employee's device.
2. The employee sends his encrypted username and password to the server.
3. The server verifies the employee‘s credentials, and the employee is connected to the network.
Using Both Client and Server Certificates
There is a potential problem in this authentication sequence—the employee verified the server’s identity, but the server didn’t verify the employee's identity. It is possible that the user stole the username and password from another employee and is using these stolen credentials on his own device.
This problem can be solved by using both a client certificate and a server certificate. Because EAP-TLS authentication employs both server and client certificates, when the employee begins authentication, the Policy Manager server sends the server certificate to the employee‘s laptop. The employee's laptop then sends the client certificate to the server.
Both the client and the server can then verify the identity of the other party and are ready to proceed: The employee sends the encrypted username and password to the server, the server verifies the employee's credentials, and the employee is connected to the network. This access process is secure.
Tasks to Obtain a Signed Certificate from Active Directory
The tasks to obtain a signed certificate from Active Directory are as follows:
1. Create a Certificate Signing Request.

2. Import the root Certificate Authority file to the Certificate Trust List.
3. Obtain a signed certificate from Active Directory.
4. Import the server certificate into the Policy Manager server.
These tasks are described in the following sections.
Creating a Certificate Signing Request
This task creates a Certificate Signing Request to be signed by a Certificate Authority (CA).
Figure 1 shows an example of the Create Certificate Signing Request page, followed by descriptions of each parameter (see Table 1).
To create a Certificate Signing Request:
1. In Policy Manager, navigate to Administration > Certificates > Certificate Store
2. Select the Create Certificate Signing Request link.
Figure 1 Create Certificate Signing Request Dialog
3. Enter the information for each of the required parameters as described in Table 1.
Table 1: Parameters for Creating a Certificate Signing Request
Parameter | Action/Description |
|---|---|
Common Name | Displays the name associated with this entity. This can be a host name, IP address, or other name. The default is the fully-qualified domain name (FQDN). This field is mandatory. |
Organization (O) | Specify the name of the organization. This field is optional. |
Organizational Unit (OU) | Specify the name of the department, division, or section. This field is optional. |
Location (L) State (ST) Country (C) | Specify the name of the state, country, and/or another location. These fields are optional |
Subject Alternate Name (SAN) | Specify the alternative names for the specified Common Name. NOTE: Specify the SAN in the following formats: email: email_address URI: url IP: ip_address dns: dns_name rid: id This field is optional. |
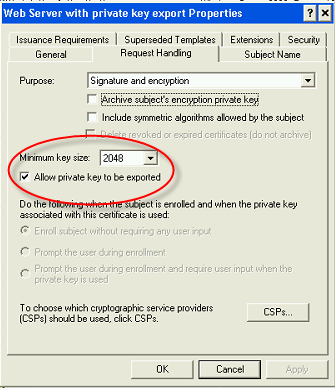
Private Key Password | 1. Enter the private key password, then reenter it to verify the password. |
Private Key Type | 2. Select the length for the generated private key types from the following options: 1024-bit RSA 2048-bit RSA 4096-bit RSA X9.62/SECG curve over a 256 bit prime field NIST/SECG curve over a 384 bit prime field The default private key type is 2048-bit RSA. |
Digest Algorithm | 3. Select one of the following message digest algorithms: MD5 SHA-1 SHA-224 SHA-256 SHA-384 SHA-512 NOTE: The MD5 algorithm is not available in FIPS mode. |
4. When satisfied with the certificate signing request parameter settings, click Submit. The Create Certificate Signing Request is generated and displayed (see Figure 2).
Figure 2 Displayed View of the Create Certificate Signing Request
5. Copy the contents of the certificate request into a text file so that you can paste it into the Directory Certificate Services web form as described in Obtaining a Signed Certificate from Active Directory.
6. To save the Certificate Signing Request file, click Download CSR.
Importing the Root CA Files to the Certificate Trust List
Make sure the root Certificate Authority (CA) certificate and any intermediate CA certificates are downloaded as separate base-64-encoded files and imported into the Certificate Trust List in Policy Managerbefore starting this operation.
To import the root CA files into the Policy Manager server Certificate Trusted List:
1. Get the root CA certificate and any intermediate CA certificates from your Active Directory administrator. This typically consists of a root CA certificate and one or more intermediate CA certificates.
2. In Policy Manager, navigate to Administration > Certificates > Trust List.
Figure 3 Certificate Trust List
3. To add the certificate file(s) to the Certificate Trust List, click Add, then browse to the root CA certificate file on your computer. The root CA certificate file is now listed in the Certificate Trust List.
Be sure to add the root CA file first, then add the intermediate CA files after you've added the root CA file. |
Figure 4 New Root CA Files Added to the Certificate Trust List
4. Make sure the Enabled column for the newly added certificate says Enabled, which is the status displayed when you successfully import a certificate manually.
5. Repeat steps 2, 3, and 4 for each certificate you received from your Active Directory administrator.
Obtaining a Signed Certificate from Active Directory
This section describes how to obtain a signed server certificate from Active Directory.
Before you begin this operation, have the copy of the Certificate Signing Request at hand, as described in Step 4 of Creating a Certificate Signing Request. |
To obtain a signed certificate from Active Directory:
1. Navigate to the Microsoft Active Directory Certificate Services page:
Figure 5 Microsoft Active Directory Certificate Services Page
2. Click Request a certificate.
Figure 6 Request a Certificate
3. Choose advanced certificate request. The Submit a Certificate Request or Renewal Request dialog opens. This request operation submits a saved certificate request to the Certificate Authority.
Figure 7 Submit a Certificate Request
4. Copy the contents of the Certificate Signing Request into the Saved Request text box.
5. In the Certificate Template drop-down menu, select Web Server. Figure 8 shows an example of the completed Certificate Request web form.
Figure 8 Completed Submit a Certificate Request Dialog
6. Click Submit. The Certificate Issued dialog opens.
Figure 9 Certificate Issued
7. Do the following:
a. Select Base 64 encoded. Base-64 encoding is used for 802.1X authentication.
b. Click Download certificate. The server certificate is downloaded to your system.
c. Be sure to note the name of the downloaded certificate so that you can identify it when you import the server certificate into the Policy Manager server.
Importing a Server Certificate into ClearPass
To import a server certificate into Policy Manager:
1. Navigate to Administration > Certificates > Certificate Store. The Certificate Store page opens.
Figure 10 Certificate Store Page
2. From the Server Certificates tab, click the Import Certificate link. The Import Certificate dialog opens:

Figure 11 Import Certificate Dialog
For security reasons, certificates signed using SHA1RSA are not recommended. Importing certificates signed with stronger keys, such as RSA with a length of more than 1024 bits, is recommended. |
Policy Manager does not support importing the HTTPS Server Certificate chain or RADIUS Server Certificate chain in P7b Base64 format. A P7B file contains only certificates and chain certificates (intermediate certificate authorities), not the private key. |
3. Specify the Import Certificate parameters as described in the following table:
Parameter | Action/Description |
Certificate Type | Server Certificate is selected by default. |
Server | Displays the name of the selected Policy Manager server. |
Type | Displays the type of server certificate that was selected: RADIUS Server Certificate HTTPS Service Certificate |
Upload Method | Select one of the following methods to upload the certificate: The Upload Certificate and Use Saved Private Key option allows the administrator to upload only the certificate. The certificate is then matched against the private key saved on the Policy Manager server. With the Upload PKCS#12 Certificate (.pfx or .p12 only) option, the administrator uploads the PKCS#12 file and provides a pass phrase. If you select Upload Certificate and Private Key Files, the administrator can choose to upload the private key file and password along with the certificate file. |
Certificate File | Browse to the certificate file to be imported. NOTE: Both certificates with a wild card as the common name and Extended Validation certificates are not recommended for use as the RADIUS/EAP server certificate. Some clients may be unable to authenticate when these types of certificates are used. |
4. Click Import. The selected server certificate is imported into Policy Manager. The Server Certificate screen displays the message: Server Certificate updated successfully. Please log in again to continue.
5. Log out of the Policy Manager server, then log in again to resume operations on this server.
Licenses are platform independent and can be installed on any controller. Installation of the feature license unlocks that feature’s functionality for the maximum capacity of the controller. Table 1 lists the license types and describes how licenses are consumed on the controllers.
License | Usage Basis | What Consumes One License |
AP | AP | An AP license is required for each operational LAN-connected, mesh, or remote AP that is advertising at least one BSSID (virtual-AP). |
ACR | Client Session | This license enables ArubaOS Advanced Cryptography (ACR) features. A license is required for each active client termination using Suite-B algorithms or protocols. |
PEF | AP | One operational AP using one or more Policy Enforcement Firewall (PEF) features, such as intelligent application identification, policy-based traffic management and controls, or stateful user firewalls. NOTE: The PEF license was called PEF-NG in some previous versions of ArubaOS. |
PEFV | Controller | The PEFV license allows a network administrator to apply firewall policies to clients using a VPN to connect to the controller. This license is mandatory for the Aruba VIA VPN client, but optional for all other VPN clients. The PEFV license is purchased as a single license that enables the functionality up to the full user capacity of the controller. |
RFprotect | AP | An RFProtect (RFP) license is required for each operational AP using one or more RF Protect features, such as spectrum analysis and Wireless Intrusion Protection (WIP). |
VMC | AP | In ArubaOS 8.0.0.0, the VMC license is a non-sharable license required to install ArubaOS as a controller on a VM. |
WebCC | AP | The Web Content Classification (WebCC) license is a subscription-based, per-AP license that supports Web content classification features on an AP for the duration of the subscription period (up to 10 years per license. |
Sharable vs Controller-Specific Licenses
Many licenses are consumed on a per-AP, or per-user basis, and are not unique to any specific hardware device. These sharable license types can be assigned to a licensing pool and used by any device within a group of managed devices. A non-sharable licenses is generated using a controller serial number, and can only be used by the individual controller for which it was generated. Both sharable and non-sharable licenses are installed using Mobility Master, allowing network administrators with root-level access to remotely add licenses to any licensing pool or managed devices on the network. For more information on adding a license to a remote managed device, see Adding a License in a Mobility Master Deployment.
Sharable via a Licensing Pool | Controller-Specific License |
|---|---|
AP | PEFV |
ACR | |
PEF | |
RF Protect | |
xSec | |
VMC | |
WebCC |
Aruba Airwave Doesn't Generate Private Key Bitcoin
Evaluation vs Permanent Licenses
Each license can be either an evaluation or permanent license. A permanent license permanently enables the desired software module on a specific Arubacontroller. You obtain permanent licenses through the sales order process only. Permanent software license keys are sent to you via email.
An evaluation license allows you to evaluate the unrestricted functionality of a software module on a specific controller for 90 days (in three 30-day increments). Evaluation licenses are added to Mobility Master and made sharable within a licensing pool. An expired evaluation license will remain in the license database until the controller is reset using the command write erase all, where all license keys are removed. An expired evaluation license has no impact on the normal operation of the controller, but it is kept in the license database to prevent abuse.
To determine your remaining time on an evaluation license, select the Alert flag ()in the WebUI titlebar. The WebUI displays information about evaluation license status. When an evaluation period expires:
Aruba Airwave Doesn't Generate Private Key Blockchain
| | The controller automatically backs up the startup configuration and reboots itself at midnight (according to the system clock). |
| | All permanent licenses are unaffected. The expired evaluation license feature is no longer available and is displayed as Expired in the WebUI. |
Perpetual vs Subscription Licenses
A perpetual license is a purchased license that has no end date; once installed, it does not expire. Most purchased licenses are perpetual licenses. The Web Content and Classification (WebCC) license is a subscription license that enables WebCC features only for the duration of the subscription (1,3,5,7 or 10 years). The subscription time period starts from the time license key is generated from the licensing Web site. Thirty days before the license period expires, an alert appears in the banner in the Mobility Master WebUI, warning the user that the license is ready to expire. After the license expiration date is passed, the license continues to operate as an active license for an extended grace period of 120 days. After this final grace period elapses, the license permanently expires.
Aruba Airwave Doesnt Generate Private Keyboard
Subscription licenses cannot be renewed. Once a license subscription expires, a new license subscription key must be generated and installed on Mobility Master. |